What Is HSTS and How Do I Implement It?
HSTS (aka HTTP Strict Transport Security) is a web security policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers should automatically interact with it using only HTTPS connections, which provide Transport Layer Security, unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in RFC 6797.
The following conditions must be met before implementing HSTS:
- For all the SSL based virtual services, SSL Acceleration should be enabled.
- The virtual services should be accessed in HTTPS protocol because the clients will not request plain text HTTP connections.
- All the sub domains of virtual services should be available before includeSubDomains is set.
- A valid certificate is required and self-signed certificate cannot be used with HSTS.
Implementation Procedures
- Login WebUI
- In SLB->Virtual Service and go to the virtual service you are going to set HSTS, click edit icon in Action column
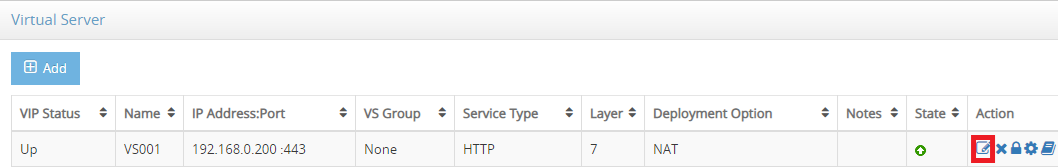
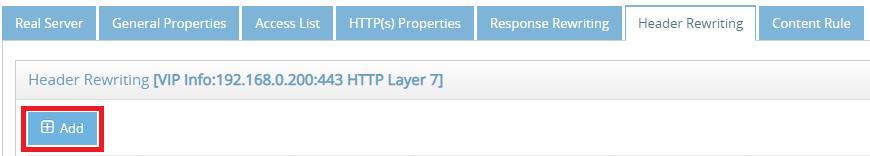
- Select Header Rewriting tab and click Add button
- In Add Header Rewriting Policy modal, input the following
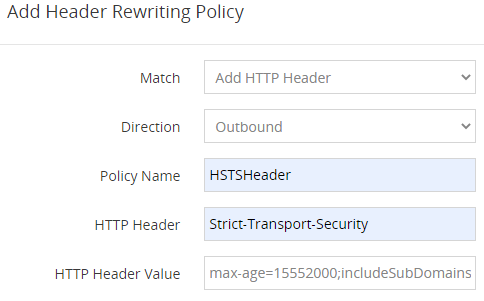
- Click Save button
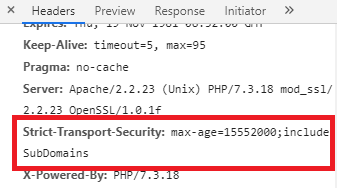
The HSTS header is Strict-Transport-Security and its possible value of HSTS includes:
- max-age This is mandatory. max-age is “time to live” field for the HSTS header, and Web browsers will cache and enforce HSTS policy for the duration of this value. max-age is a value in seconds up to a maximum of 31536000 (365 days) and a value of “0” will disable HSTS. We recommend 15552000(6 months) in order to earn an A+ rating from Qualys SSL Labs.
- includeSubDomains This is optional. If set, it will include all sub-domains in the HSTS policy as well. You need to make sure that all the services using subdomain must be using https.
- preload This is optional. HSTS preloding is a mechanism whereby a list of hosts that wish to enforce the use of SSL/TLS on their site is built into a browser. You need to submit your site at hstspreload.appspot.com before using preload.
Please note that HSTS is the policy cached in each browser. If you configure HSTS settings, browsers will cache those settings for the duration of max-age. In the example above, we set 6 months. If your site becomes inaccessible over strongly-configured HTTPS, web browsers will refuse to connect to the site on HTTP until the policy expires in the browser. Therefore, it’s important that you set up HSTS only after establishing a stable SSL configuration.
Verify HSTS Headers
There are couple of easy ways to verify if HSTS is working on the virtual services.
- Use Google Chrome to access your virtual services, for instance, https://demo.test.com
- Launch Chrome Developer tools
- Select Network tab
- In Response Headers section, you should see HSTS header